Report of the Independent Investigation of Alleged Wrongdoing in Lew-Adelstein Hand and Audit of Security of ‘Hustler Casino Live’ Stream, Commissioned by High Stakes Poker Productions, LLC
December 14, 2022
Bulletproof, a GLI Company
The Solution Group, Legal and Private Investigation
Sheppard Mullin Richter & Hampton LLP
Introduction
On September 29, 2022, one of the most controversial hands in poker history was played on an episode of “Hustler Casino Live,” which streams high-stakes poker games played at Hustler Casino in Gardena, Calif., to a worldwide audience on its YouTube Channel. The hand has subsequently been viewed by hundreds of thousands, if not millions, of poker fans around the globe. In the hand, recreational poker player Robbi Jade Lew called an all-in shove by Garrett Adelstein for her remaining $109,000 with the jack of clubs and four of hearts on a board reading ThTc9c3h. Lew ended up winning a pot of $269,000 when her jack high held against Adelstein’s eight of clubs and seven of clubs. After the hand, Adelstein said he was suspicious of Lew’s play and she agreed to return half the pot to him. In the weeks that have followed, Lew has repeatedly denied wrongdoing and requested that Adelstein return her winnings. In October, Adelstein published a series of allegations on the Two Plus Two poker forum that he said proved Lew “was very likely part of a cheating ring of at least three members,” which he said likely included Lew, a friend of hers who was playing that night and an employee of the company that produces the show. Adelstein and others in the poker community said that there was no logical reason why Lew would call a bet of that size without inside knowledge that she had the better hand. Her hand would lose to any pair as well as many potential bluffs, including ace-high, king-high, queen-high or better jack-high hands. In fact, Adelstein’s exact hand was one of the few combinations of hands that he could have had that she would beat. Lew offered several explanations for her call on Sept. 29 and in the weeks that followed; most of her explanations centered on the fact that she thought Adelstein was bluffing, or as she said on Sept. 29, “You don’t have shit.”
On October 1, 2022, High Stakes Poker Productions (HSPP), which owns and operates “Hustler Casino Live,” issued a statement that said it would conduct a comprehensive investigation, including staff and player interviews, a review of stream video and Hustler Casino surveillance video as well as “an investigation by a third-party cybersecurity company that will leave no stone unturned within our system.” HSPP said that once the investigation was completed it would release the findings publicly – no matter what they revealed. As promised, HSPP hired a cybersecurity firm, a law firm and a private investigations firm to conduct a detailed investigation. This report documents the findings of the investigation.
Methodology
Shortly after the hand in question, HSPP retained cybersecurity firm Bulletproof, a GLI Company, to conduct an audit of HSPP livestream operations, procedures, equipment and vulnerabilities, and to search for any evidence of wrongdoing in the Sept. 29 hand. Bulletproof, owned by New Jersey-based GLI, has decades of experience analyzing technology, security and compliance in numerous industries, including top gaming organizations, lotteries, tribal organizations and government agencies to mitigate risks and improve security of its clients’ operations. Bulletproof was given complete access to “Hustler Casino Live” facilities, including its production room, the poker table, stage, and all equipment used in producing the show. A Bulletproof employee was allowed to observe the production of two episodes of the show as part of its investigation. The firm also interviewed HSPP owners Nick Vertucci and Ryan Feldman. Acting on Bulletproof’s recommendations, HSPP made multiple improvements to strengthen the security of the production of “Hustler Casino Live.” Those improvements will be addressed later in this report.
HSPP also retained The Solution Group, a Los Angeles-based legal and private investigations firm, to conduct interviews and provide research as part of the investigation. More than a dozen interviews were conducted by The Solution Group. On the advice of legal counsel, polygraph testing was not conducted.
Hustler Casino management also assisted in the investigation, reviewing surveillance video and sharing its findings with the investigative team.
Legal support was provided by the Los Angeles office of international law firm Sheppard, Mullin, Richter & Hampton.
Cybersecurity and Technological Audit
HSPP contracted Bulletproof, a GLI company (Bulletproof) to perform an assessment of its livestream operations, procedures and equipment to locate weakness in the systems, identify improvements and provide information to HCL in regard to the events of Sept. 29, 2022.
Bulletproof is a component of the GLI Capital Group, which includes Gaming Laboratories International, the premier independent test lab for the gaming sector. Having decades of technology, security and compliance expertise, Bulletproof works within many industries including top gaming organizations, lotteries, tribal organizations, and government and state agencies to mitigate risks and improve client processes, systems and business infrastructure.
Bulletproof has explored and listed alleged methods to cheat the “Hustler Casino Live” system and how it can be done. In cases where it is not scientifically possible, a brief technical overview will be given. The table below summarizes the areas Bulletproof examined as well as its analysis.
Bulletproof listed and provided an opinion on the estimated priority of the issues identified, ranging from Low to High, and the estimated complexity that would be faced by an attacker trying to exploit the issue, ranging from Easy to Highly Complex (Table 1).
The assessment of HCL’s systems and security controls are inconclusive in determining if cheating occurred. It should be noted that a lack of evidence does not imply cheating did or didn’t occur. However, Bulletproof did inspect all systems and physical equipment and identified multiple improvements that will help improve security of the game and increase confidence to HCL, the players and the public.
Bulletproof was able to recover key elements from Sept. 29 (e.g., programs ran, USB keys plugged in, software installed). Upon inspection of the systems, table and network, there was no evidence of tampering, remote access, viruses, rogue hardware installed, or previously installed programs on the machines that are used daily.
It was also evident upon inspection of policy and setup that HCL had implemented some security measures prior to Sept. 29:
-
-
- Cell phones and electronics were prohibited in the booth. Players were prohibited from possessing cell phones or smart watches at the table.
- Systems were segregated between those that need to be connected to the internet, such as the live commentator’s PC and the streaming PC, and those that did not.
- All other systems that were used for sound, video mixing and the GFX server were on a private non-internet accessible network.
- Data was transferred between the production mixing machines all the way to the streaming PC via video cable and not a network.
- HCL did turn off broadcasting of its Wi-Fi access point, limiting basic attacks and enumeration.
-
With security practices and policies, there should always be a balance between security and usability; in HCL’s case, there must also be a balance between security, production quality and showmanship. All systems require one or more trusted individuals to manage and run the system. For the purpose of this report, the trusted individual shall be the business owners or systems administrator. There should always be a minimum of two trusted individuals with administrator access for redundancy and security purposes. Segregation of duties, security logs and tamper prevention help address and mitigate security events and collusion within the organization and its administrators.
HCL, its players and its audience should understand that no security solution or process can completely solve mechanical or electronic game cheating because methods and technology are continually evolving. With those changes, security, technology, processes, and yearly audits also need to be kept up. The more difficult it is for an insider or player to cheat the system, the more they are likely to move on. But a balance must still exist.
Bulletproof Analysis of HCL Equipment
Poker Table
Bulletproof inspected all elements of the poker table for tampering and transmission devices and found no evidence of tampering. This included a dismantling of the table (Figure 1) and a thorough inspection for any vulnerabilities or signs of wrongdoing. It is Bulletproof’s opinion that there is not adequate room for additional devices to be placed in the table that could evade detection.
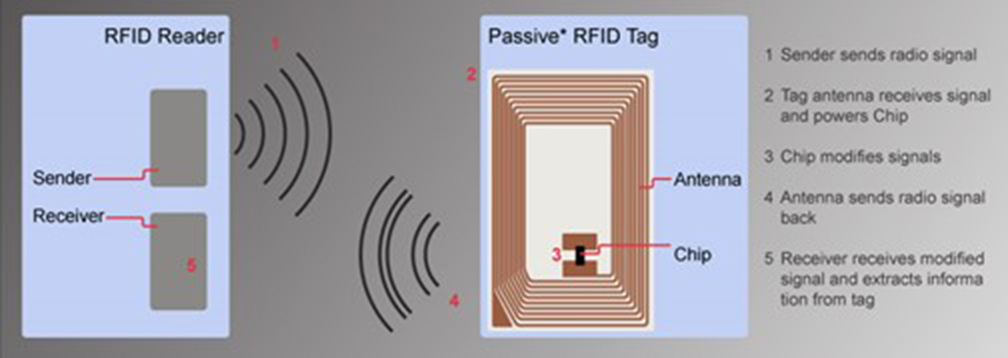
RFID
The RFID system on the table uses a HF (high frequency) card reader to read the Faded Spade® playing cards manufactured. The cards are each embedded with a Mifare Ultralight EV1 antenna and chip that operates at 13.56 MHz as defined by ISO 1443A. Mifare Ultralight Ev1 in this implementation is a passive RFID rather than an active RFID. Passive RFID requires an external reader to provide power to the embedded card antenna, known as the forward channel, which provides wireless power to the card’s antenna powering the RFID chip; in comparison, active RFID contains its own power source.
Once the RFID is charged, the chip then broadcasts its information back to the reader (Figure 2). This signal is known as the backchannel. Mifare Ultralight EV1 has a maximum transmit distance of up to 10 cm on the low end of 13.56; however, the tester was able to reach up to ~30 cm. It is a common misconception that all RFID tags can be captured at a distance. Some tags on different bands can reach between 100 m and 200 m when the application requires it, but this usually requires an antenna configured to capture a wide range of RFID tags at once, such as those used on a toll road or warehouse inventory where many RFIDs need to be read at once.
There are two ways an attacker can try to read a Mifare Ultralight EV1 at a distance over 10 cm:
-
-
- Using a very large directional antenna, specialized equipment and a good amount of power and tuning to snoop the cards’ signal while it is charged by the reader.
- Using a large, directional antenna to send a charge over a distance to power the RFID card and capture the back-channel data.
-
Extensive research has been conducted in recent years into methods that would increase the reading distance of Mifare and other bands. Due to the limitations of transmit distance, researchers have not been able to reach over a few meters. Attacks of this nature were largely focused on capturing credit card chips and other ID information without having to get within a few centimeters of the RFID chip.
A problem with applying these scenarios to an RFID poker table—aside from the antenna tuning, Electro Magnetic Interference (EMI) and power problems—is that there are multiple cards on the table, including those in the dealer’s hands, that would also be read by a strong enough reader that is sending a forward-charging signal. Furthermore, an attacker would have to catalog each card’s value by its encoded Universal Unique Identifier (UUID) on all card decks and have it readily available to translate to the card value. If a device was strong enough to charge the coils on the playing cards from a distance, it would charge all the cards in its path, including the ones in the dealers’ hands which are around 1 inch from the 9th seat’s cards.
To capture data from a card that has a maximum broadcast range of 10 cm, you would need to be on the same horizontal plane as the card reader with a customized antenna and power source. Bulletproof is not aware of a system that could be concealed in an object or hidden in the building’s infrastructure that could accurately sniff multiple RFID cards from over 30 cm. This is assuming perfect conditions without EMI present, antenna tuning has been performed and discounting the other cards on the table or the dealer’s hand. A researcher and fellow at the IEEE, G.P. Hancke, was able to capture the RFID card backchannel on ISO 14443A 13.56 MHz from 3 meters using specialized equipment and antennas as seen in Figure 3. There has been some speculation as to whether a water bottle or other device on the table Sept. 29 could have been used to intercept RFID signals. Based on the above, such a scenario is extremely unlikely.
Card Shuffling Machine
Bulletproof inspected the card shuffler for tampering and the presence of a remote eavesdropping device. The shuffler is a DECKMATE 1® manufactured by Shuffle Master. The general rule in cybersecurity is if a device knows the value of an object, then an attacker can know that object’s value. The DECKMATE 1® cannot read any information about the cards other than the number of the cards in the deck. It is therefore concluded the DECKMATE 1® is safe for HCL poker play. Bulletproof recommends tamper-evident tape also be used to seal the case and inspected before each game by the dealer or any HCL staff as an additional security measure.
Production Booth and Operations
Bulletproof inspected the production booth and systems over the weekend of October 14-16 during non-production hours accompanied by HCL staff and observed two livestreaming events from the production room. The production booth and cables were inspected for man in the middle (MITM) devices on the network and USB ports. MITM devices allow attackers to monitor machine communications and sometimes interfere or change data. All video HDMI cables were also inspected for MITM devices, such as the HAK5© Screen Crab, which is designed to wirelessly send timed screenshots of the current content on the monitor to the attacker. No MITM devices were found during the inspection.
Bulletproof identified some critical risks with the room setup and broadcast operations:
-
-
- The live cards could be seen by anyone in the production room just by turning their head. This was tested and observed during a show from the production room. However, the live hole and community cards could not be seen from the commentator room, even if the curtain was open, without the help of a visual aid such as binoculars. The GFX Station could not be seen from the announcer room due to the server rack blocking the angle.
- The announcer was observed leaving the production area to use the facilities during live play; as a result, he could have seen the live cards on the live production screens.
-
Since that time, HSPP, in consultation with Bulletproof, reconfigured the production room and made other modifications to significantly improve security and reduce the opportunity for anyone other than the show’s owner/director to view cards in real time. All workstations were turned around so that the computer screens cannot be viewed from the rest of the room. Only one monitor now displays the hole cards and it can only be viewed by the director. A door was installed, which is closed and locked throughout the stream, preventing anyone from entering the room. Even if anyone entered the room (which is prohibited), they would only see the back of the monitor used by the director – they would not be able to view hole cards. Other protocols implemented will be discussed later in this report.
Network, PC Workstations and Systems
Bulletproof inspected the studio’s network, servers, and desktop PCs. The internet router was designed for the home or small office and therefore is not sufficient for storing logs and does not contain many custom security features. The internet router also has wireless built in. For necessary maintenance reasons and Windows patches, all PCs can connect to the wireless internet network. All users can connect to the private network at the same time as the internet wireless. While precautions were taken to guard the password, the PCs have passwords saved locally so the user isn’t required to enter a password to join the network. Furthermore, the current Wi-Fi password is weak and can be hacked over the air.
It should be noted at the time of Sept. 29, 2022, the logs show the Wi-Fi on all systems was off, leaving only the streaming and announcer PCs as the only ones on the Internet on Sept. 29. Due to lack of firewall logs and router access, Bulletproof is unable to determine if other Wi-Fi devices were connected at the time or what remote sites were accessed.
On the recommendation of Bulletproof, HSPP agreed to remove Wi-Fi on all systems.
PokerGFX Server, Action Tracker System and Communications
The PokerGFX system runs on the Windows operating system platform. Upon execution, it checks the Windows and PokerGFX configuration for the proper security setup and will warn the user if there are potential security risks. Because of the production quality of the stream, some of these security features are bypassed on purpose; most notably, the hole cards are displayed in real time, which is necessary for the mixing process with focused player sound and split camera views. The final mix is then broadcasted on a delay.
The PokerGFX system was inspected for malware, installed programs and system logs. It was found that no remote control or viewing software was installed at the time of the broadcast on Sept. 29, 2022 on all systems showing hole cards except for the control machine used to display multiple machine screens. No USB keys, foreign devices or wireless connections were active on the system at the time of Sept. 29, 2022. This information was obtained with a forensic image and specialized software.
The current PokerGFX system is configured for USB communications from the table to the server. Bulletproof captured some of the USB traffic by installing software on the GFXServer to monitor it while hole cards were being placed on the table. Bulletproof was unable to decrypt the communications because specialized hardware would be required to do so. Bulletproof was able to capture the USB traffic by installing software on the GFXServer to monitor it while hole cards were being placed on the table. However, if an attacker is already on the GFXServer, there would be better avenues of attack such as remote screen monitoring.
Capturing USB traffic between the table and the GFXServer requires a highly specialized device, debugging/programming skills, and installed in-between devices on the wire. USB 2.0 specification limits the length of a cable between two devices to be in the range of 5 m.
The table hardware converts USB-A to RJ-45 using power from the USB port on the table, then back to USB-A when it reaches the server. RJ-45 is a small, shielded cable with 8 wires most commonly used in network systems. It is sometimes run through conduit, which is done in this case at the base of the HCL table. USB-A is a type of connector that is used for USB 1.0 and 2.0.
Bulletproof verified details on the encryption methods with the developer of the GFXPoker system; however, further analysis or code review was outside the scope of the audit.
These are the top risks Bulletproof identified:
-
-
- All non-streaming machines are connected to a private network that has no internet access but can be joined to the wireless network by the logged in user.
- The user and password are shared amongst staff and staff has full administrator access to the system.
- The antivirus license is expired.
- No tracking of users, actions, and internet access stored in a log file.
- The System BIOS is not password protected.
- No website tracking or user access control is utilized.
- Non-commercial grade network gear and router used lacks features for network security, segmentation, and logging.
-
Production Communications
HCL is currently using the Clear-Com FreeSpeak II system, which runs on the 1.8Ghz and 2.4GHz frequency bands. The current system is vulnerable to eavesdropping with specialized equipment such as a Software Defined Radio (SDR) or specialized parts that are not easily found anymore or needs to be built from scratch. A potential attacker would have to have advanced knowledge of radio and engineering to craft or program a device capable of eavesdropping. While this is possible, it is very unlikely and not the most effective attack compared to other easier avenues discovered by Bulletproof.
Player Security
Bulletproof examined some potential methods that bad actors might have used to exploit HCL security. Bulletproof does not know whether any of these methods were used on or before Sept. 29, 2022. The scenarios and methods detailed below are theoretical.
TENS Unit or Other Personal Remote Devices
As previously mentioned, Bulletproof could not test every available personal device on the market. Instead, a remote-controlled TENS unit was used as the control for multiple distance scenarios.
Radio-controlled remote devices either use Bluetooth or other radio frequency devices such as a handheld remote. The radio frequencies of both devices greatly vary with distance, objects in the room and signal strength.
Personal devices that are internet-enabled for remote control by remote users usually need to be connected though the device wearer’s phone’s internet connection as the software and Bluetooth connection are paired with the device from the phone or electronic watch. The remote user accesses the phone software via another app or through a web browser. Because of the size of the devices and the batteries used, personal devices need a phone’s Bluetooth connection as it would be too expensive and difficult to build with a Wi-Fi enabled antenna and difficult to pair with a Wi-Fi router due to a lack of an interface on the device. In researching, Bulletproof could not find a device that didn’t require a Bluetooth-enabled phone for the device wearer in order to give a remote user access from a long distance. While Bulletproof couldn’t test every possible device or custom build one, there are devices created for cellular communication such as an Apple or Android watch which can easily be hidden on a person without the wristband attached. There are features on watches that would allow a sender to send haptic feedback taps from one watch to another from anywhere in the world.
Aside from cell phones or Bluetooth devices, potential attackers could utilize remote control operated devices that use different wireless band. Most remote controls we have found have a short distance 0.3 m to 9 m in perfect conditions. Perfect conditions are defined as no barriers or walls containing metal and concrete or other objects in between.
Bulletproof tested a TENS unit with a remote that advertised it would work up to 9 m. Bulletproof tested in a few different controlled environments to measure the reliability distances, including a scenario with a straight line of sight and one behind a concrete firewall.
In testing with an assistant with a straight line of sight and no objects in between, the Bulletproof tester was able to use the TENS unit up to 10 m. When the tester then tried standing behind object such as a wood door, concrete, or a similar firewall structure in the production room, they were only able to reach up to 5 m away from the remote and 7 m behind a wooden door before the remote became ineffective.
Most electronic personalized units have a safety shut off timer when not actively in use or if the remote signal on a remote control is lost. In this scenario, the user would have to turn the unit back on, which usually gives an audio cue such as a beep. However, someone could technically remove the speaker or cover it by opening the device.
With some complexity, there are many ways to make custom hidden remote signaling devices with parts found and hobbyist instructions that can be hidden anywhere. However, these parts require an antenna, a battery and pneumatic or sound-producing mechanisms.
Bulletproof’s opinion is by strengthening the production booth per the previous recommendations to ensure information cannot get out electronically or personally will render most remote signaling devices useless. However, it is still recommended that players be checked for devices and leave their personal belongings in a secure area. For the security of the player, each should be given a signal-blocking Faraday bag in which they can place their bags, phones, and all other personal items which will be kept in the corner on stage. Faraday bags (Figure 4), just as the production booth, should be tested before utilization as cell tower distance can affect results.
Bulletproof’s Conclusions
Key findings include: 1) The Deckmate shuffling machine is secure and cannot be compromised; 2) It’s extremely unlikely that any card-reading device could have been stored in a water bottle or other object on the table; 3) RFID technology used by “Hustler Casino Live” is safe. Any device that intercepted a signal would receive a serial number, not the actual card; 4) Radio communication to the on-floor camera operator is not an issue; 5) The PokerGFX system was free and clear of malware, installed programs or systems that could intercept hands.
While no direct evidence of cheating was found, Bulletproof found that cheating with the Sept. 29 setup was possible. Most methods of cheating the system can be avoided by tightening security in the broadcast booth, which HSPP has done.
With the production booth secured, then all the other methods, such as electronic signaling, become less relevant. This is securing at the most important level first, which is the source; afterwards, additional security can be applied all the way down to the player level.
Summary of Security Improvements
HSPP has implemented the following improvements, among others, to increase the security of the “Hustler Casino Live” stream:
-
-
- HSPP reconfigured the production room so that only one monitor can display hole cards, and it can only be viewed by the director.
- A wall and door were installed to the production room; the door is kept closed and locked throughout the stream. Only HSPP has the key to the room.
- Production room employees must surrender mobile telephones and other electronic devices, which are kept in signal-blocking Faraday bags, before entering the production room.
- Pre-employment background checks will be performed on all prospective employees.
- All players must surrender their telephones, smart watches and other electronic devices before playing in the game. Other personal items are stored in signal-blocking Faraday bags and kept away from the table.
- Players are required to sign waivers agreeing that they have no financial investment in any other players in the game.
- Security personnel use a metal-detecting wand to screen players each time they enter the stage area. Players who leave the stage for any reason are re-screened before re-entering the stage.
- Remote camera operator is no longer on open-production channel; the only way director can communicate with that person is to press a button to communicate directly with them.
- Security video camera systems record all employees in production room from multiple angles. Security cameras will not view hole cards on director’s monitor.
-
Player, Employee and Witness Interviews
As part of the investigation, HSPP retained The Solution Group, a Los Angeles-based legal and private investigations firm, to interview players, employees and third-party witnesses who might have information about the Sept. 29 hand.
Investigators from The Solution Group conducted more than a dozen interviews of players, HSPP employees and third parties about the Sept. 29 livestream game, including Ms. Lew, Mr. Adelstein, Jacob “RIP” Chavez, Bryan Sagbigsal, Bart Hanson, Darren “Beanz” Attebery, William “Billy” McMahon, Nikhil “Nik Airball” Arcot and others.
These interviews failed to produce conclusive evidence of wrongdoing.
As HSPP previously disclosed, during the course of the investigation Hustler Casino staff uncovered video evidence that HSPP employee Bryan Sagbigsal stole $15,000 in chips from the stack of Ms. Lew after play had concluded on Sept. 29 while Ms. Lew was away from the table. HSPP terminated the employment of Mr. Sagbigsal after discovering the theft and contacted the Gardena Police Department.
During an interview with HSPP and its legal counsel, Mr. Sagbigsal admitted that he stole the chips and apologized. He said he acted on his own out of financial desperation and repeatedly denied that he was involved in cheating or that he collaborated with any players.
Initially, Ms. Lew told Gardena police detectives that she did not wish to pursue criminal charges against Mr. Sagbigsal. She later changed her mind and asked Gardena police to pursue a criminal prosecution. At the direction of Ms. Lew, Gardena police detectives investigated the theft of her chips and eventually obtained an arrest warrant for Mr. Sagbigsal. On November 22, the Los Angeles County District Attorney’s Office charged Mr. Sagbigsal with two counts of felony grand theft (Los Angeles County Superior Court Case Number YA106932). A copy of the DA complaint is attached to this report is available here.
As of the date of this report, Gardena police have not arrested Mr. Sagbigsal.
Solution Group investigators were not able to identify any prior relationship between Ms. Lew and Mr. Sagbigsal. Hustler Casino staff said surveillance video also failed to provide evidence of an inappropriate relationship between Ms. Lew and Mr. Sagbigsal.
As previously disclosed, HSPP has offered to refund the $15,000 to Ms. Lew. That payment is expected to occur before December 31.
Our investigation confirmed reports that prior to his employment with HSPP, Mr. Sagbigsal had a criminal record, including a conviction for robbery. High Stakes Poker Productions did not conduct a pre-employment screening of Mr. Sagbigsal, something that could have identified his past criminal record. In the future, HSPP will pay a professional agency to search databases to determine whether any applicants have criminal records. HSPP will also perform periodic financial and credit checks of employees.
Our investigation found that Mr. Sagbigsal failed to claim a bounty of more than $200,000 that had been offered by members of the poker community to anyone who would disclose firsthand knowledge of any cheating on the stream. No one else stepped forward to claim the bounty. It is important to note that anyone who disclosed participating in a criminal scheme could face prosecution, so the fact that no one came forward to collect the bounty does not prove that no wrongdoing occurred.
Garrett Adelstein Allegations
In October, Mr. Adelstein published a series allegations on the Two Plus Two poker forum that he said leads him to believe that Ms. Lew “was very likely part of a cheating ring of at least three members, including her, RIP, Bryan and potentially others.”
Investigators reviewed these allegations, including Mr. Adelstein’s claims that video evidence showed “RIP and Robbi allegedly working together to cheat during these games,” and that Mr. Chavez had provided Ms. Lew money to gamble with that night in exchange for a share of her winnings – without disclosing that arrangement to the rest of the players or the show’s producers.
While Mr. Chavez and Ms. Lew appeared to communicate with each other at the table on Sept. 29, the investigation found no evidence that they shared information about their or other players’ hands while a hand was in play. Further, our investigation failed to uncover evidence of any communication between Ms. Lew and Mr. Sagbigsal before, during or after the Sept. 29 hand.
Still, the undisclosed financial relationship between Ms. Lew and Mr. Chavez creates the appearance of collusion between the two players. Such conduct is widely considered unethical in the poker community and is prohibited in “Hustler Casino Live” games. In order to prevent such conduct in the future, all players are now required to sign a waiver agreeing that they do not have investments in, or agreements to share their profits with, other players in the game. The waiver can be viewed here.
Hustler Casino Investigation
The Hustler Casino surveillance team reviewed video from the day of Sept. 29 and found no events of interest in or around the production room. Surveillance video showed no suspicious interactions among the players and/or employees away from the table.
Conclusion
When the integrity and security of its livestream poker game was called into question on September 29, High Stakes Poker Productions went to great lengths to determine if any evidence of wrongdoing could be found. HSPP has spent more than $100,000 and significant hours of its time to conduct a thorough investigation. Based on the findings of cybersecurity experts, interviews with players, employees and third parties, a review of video of hands played on the show and surveillance video inside the casino and parking lot, no conclusive evidence of wrongdoing related to the Sept. 29 hand was found. That does not mean that no wrongdoing occurred; it means that the investigation failed to find credible evidence of wrongdoing. The extensive review of HSPP’s technology, equipment and protocols did uncover improvements that could be implemented to improve the security of the “Hustler Casino Live” stream. In consultation with its experts and legal counsel, HSPP has made numerous improvements that will increase the safety and security of its stream and ensure that “Hustler Casino Live” can continue to provide safe, secure and entertaining poker free of charge for the world to enjoy.
###